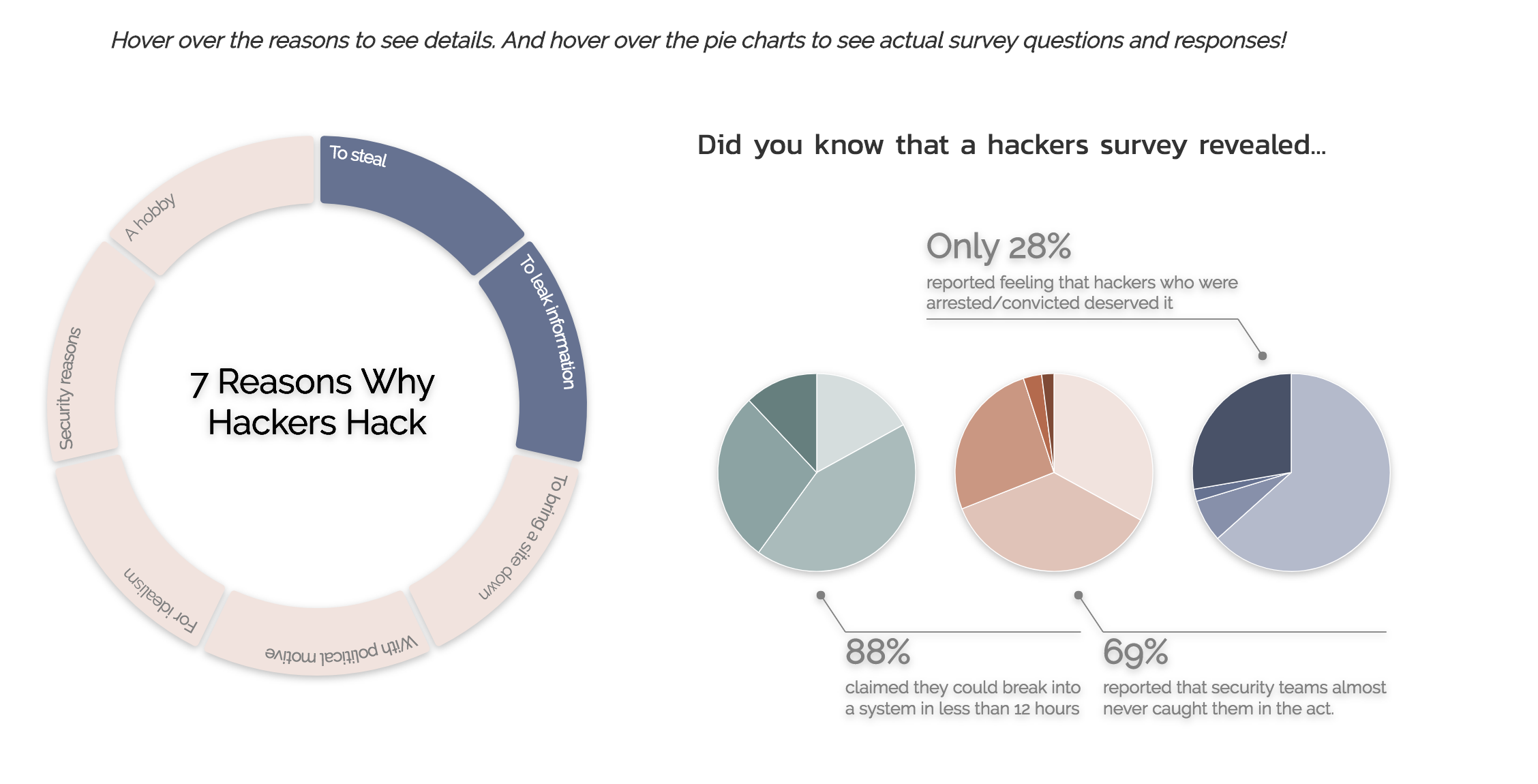
PDF) Overview of Ethical Issues such as security, confidentiality and Hacking in software engineering

White hat Metasploit Project Exploit Computer security Penetration test, Framework, logo, payload, security Hacker png | PNGWing

White hat Metasploit Project Exploit Computer security Penetration test, Framework, logo, payload png | PNGEgg
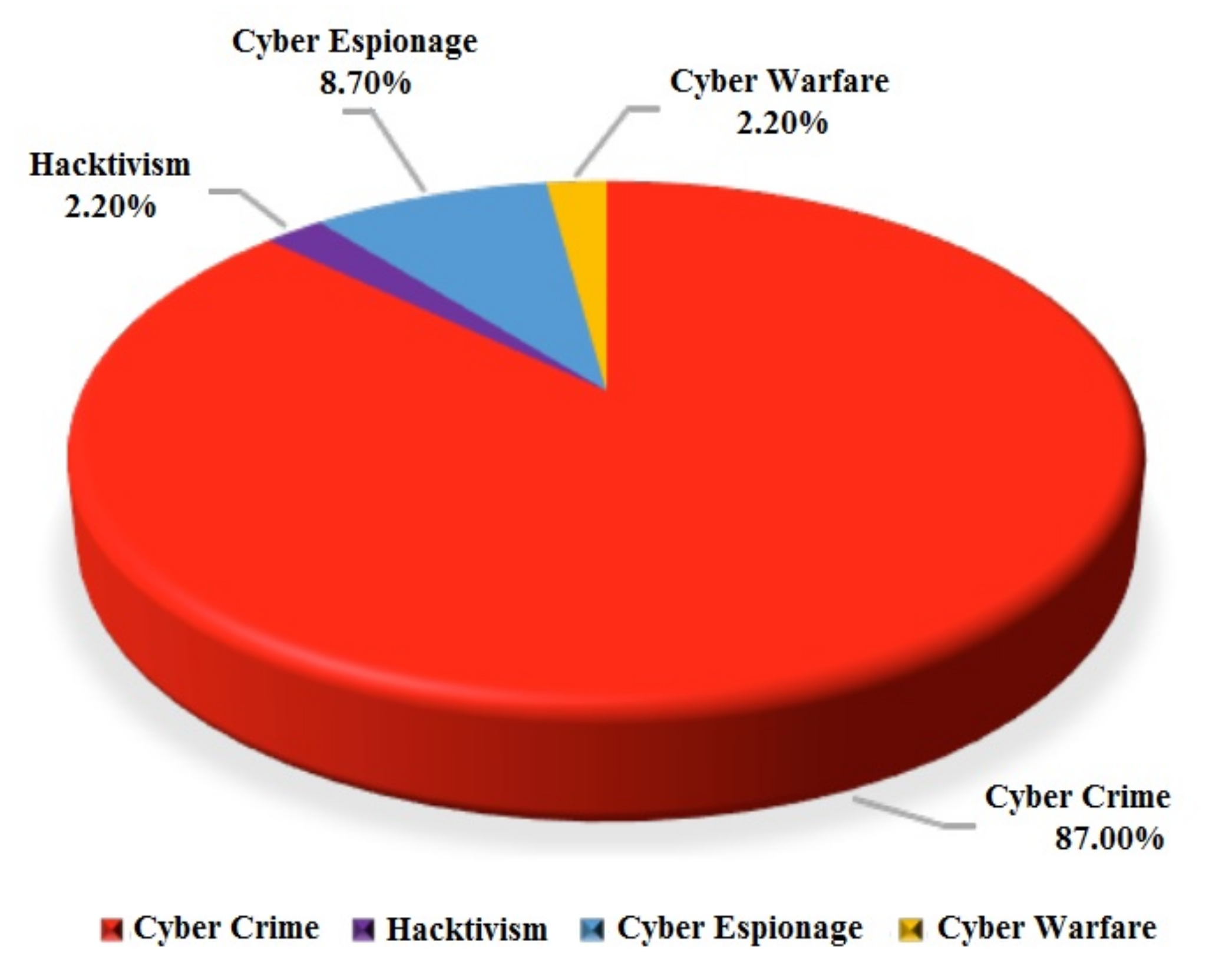
Applied Sciences | Free Full-Text | Internet of Things Meet Internet of Threats: New Concern Cyber Security Issues of Critical Cyber Infrastructure | HTML