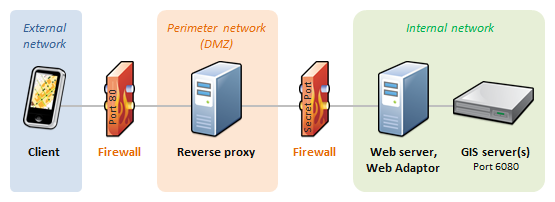
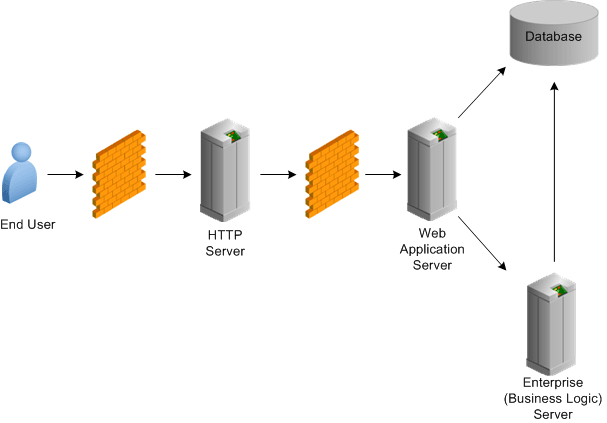
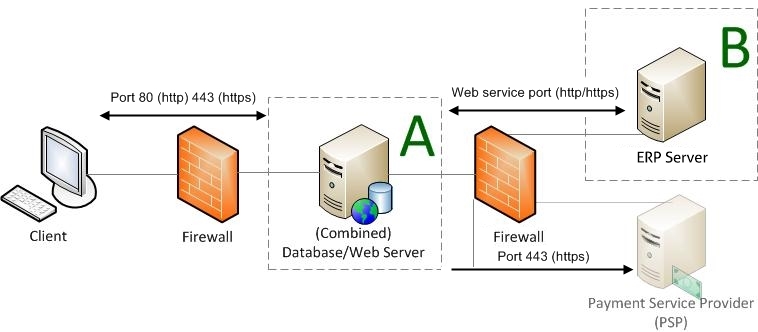
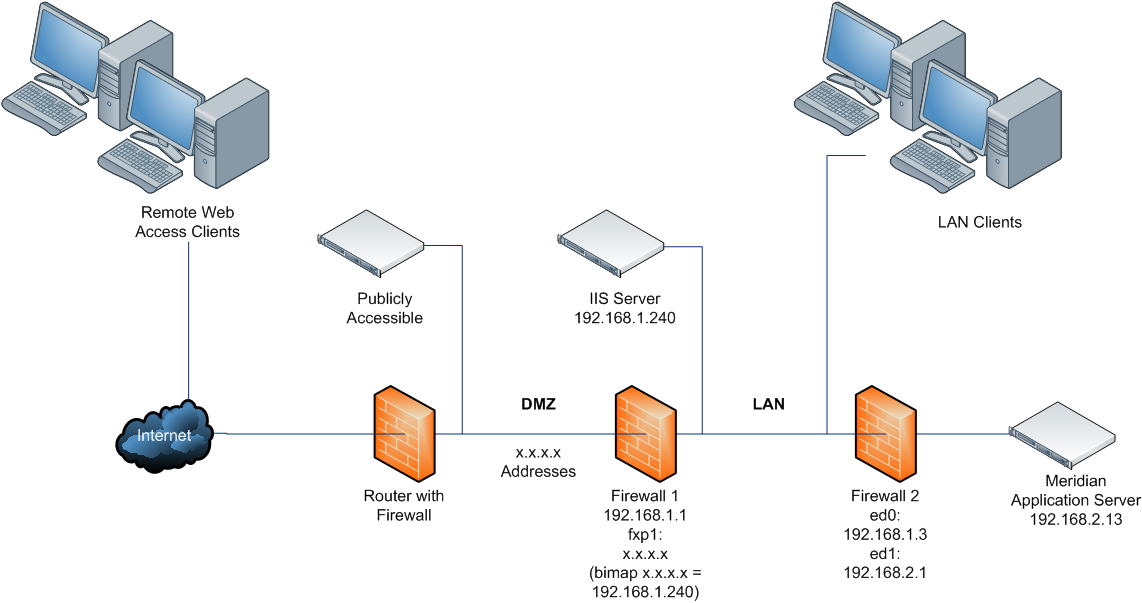
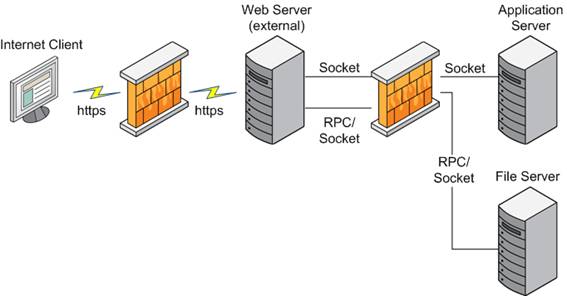
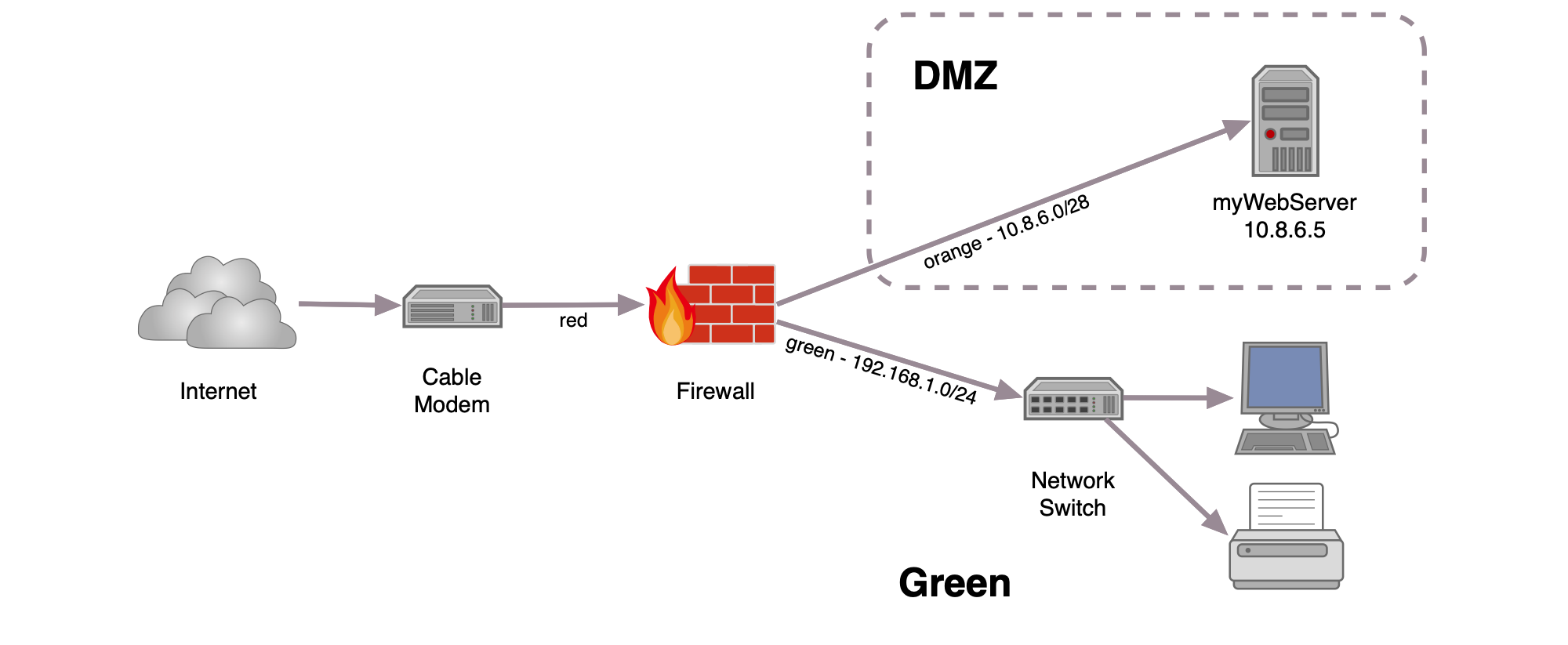
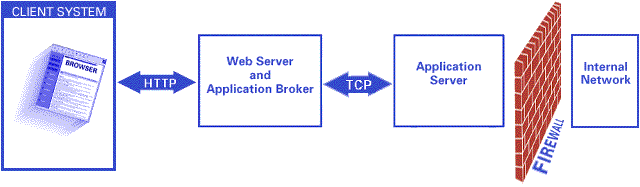
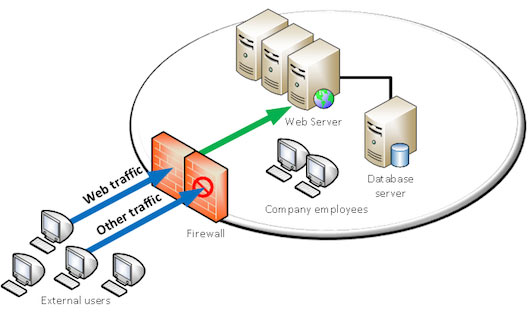
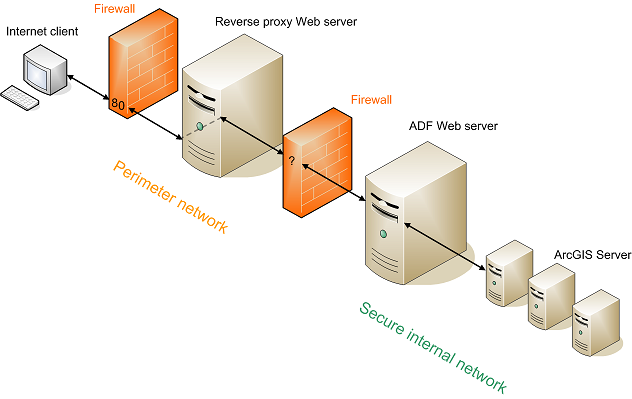
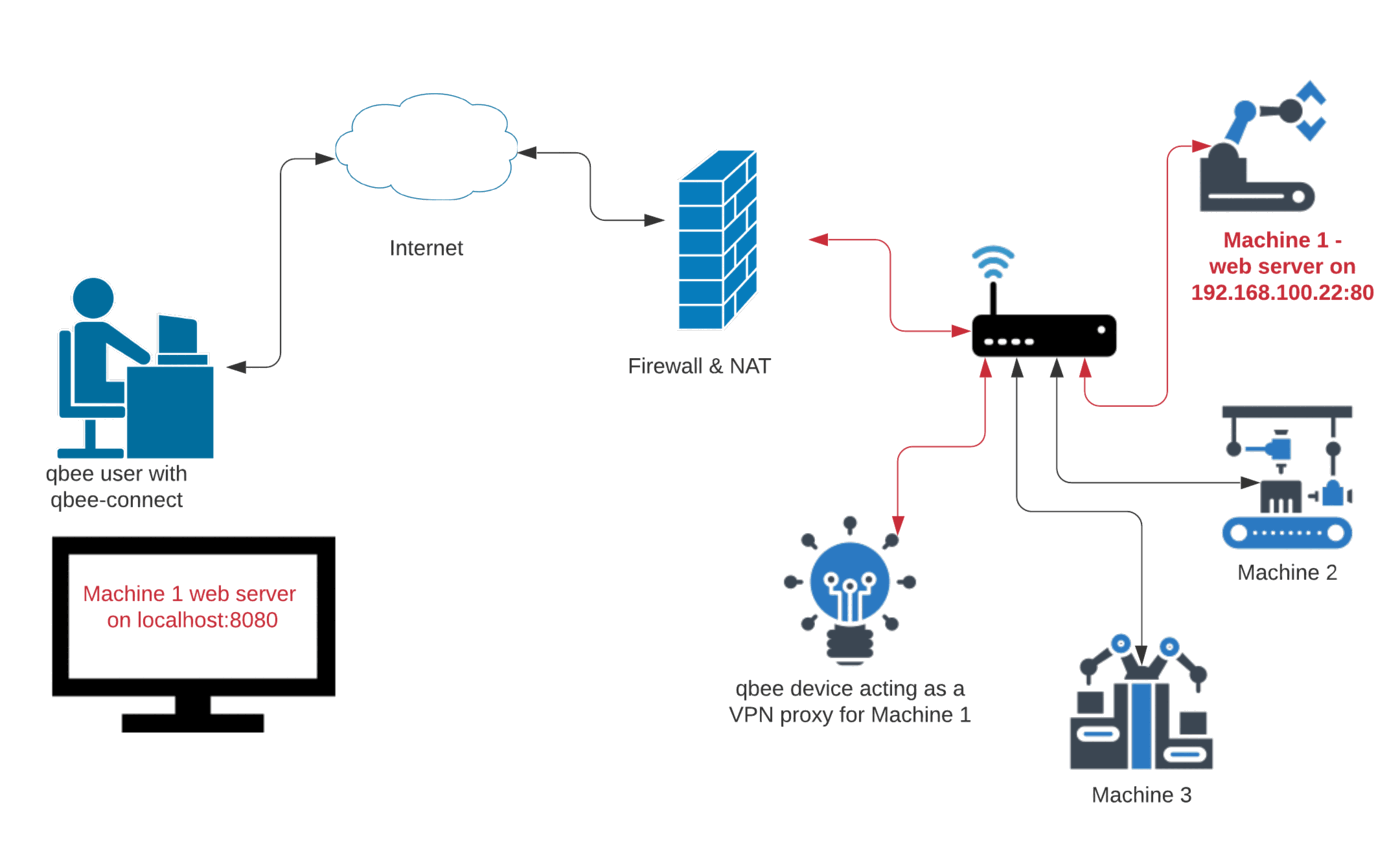
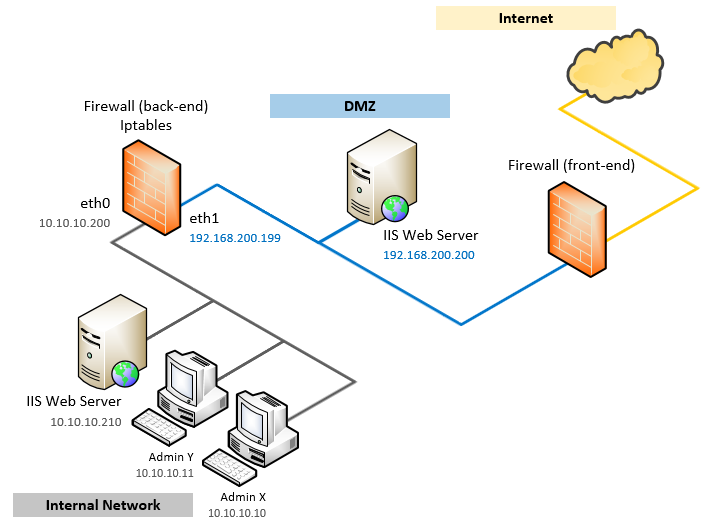
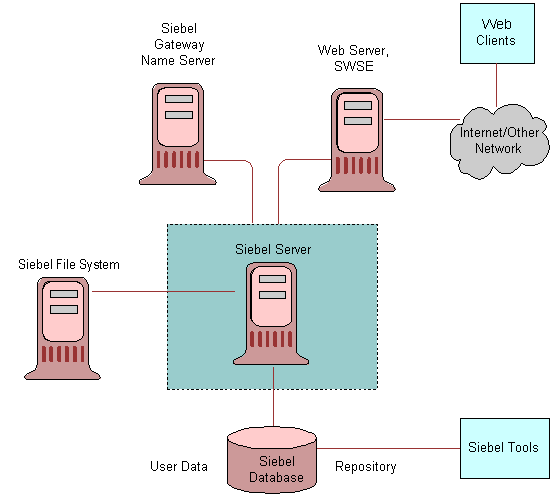
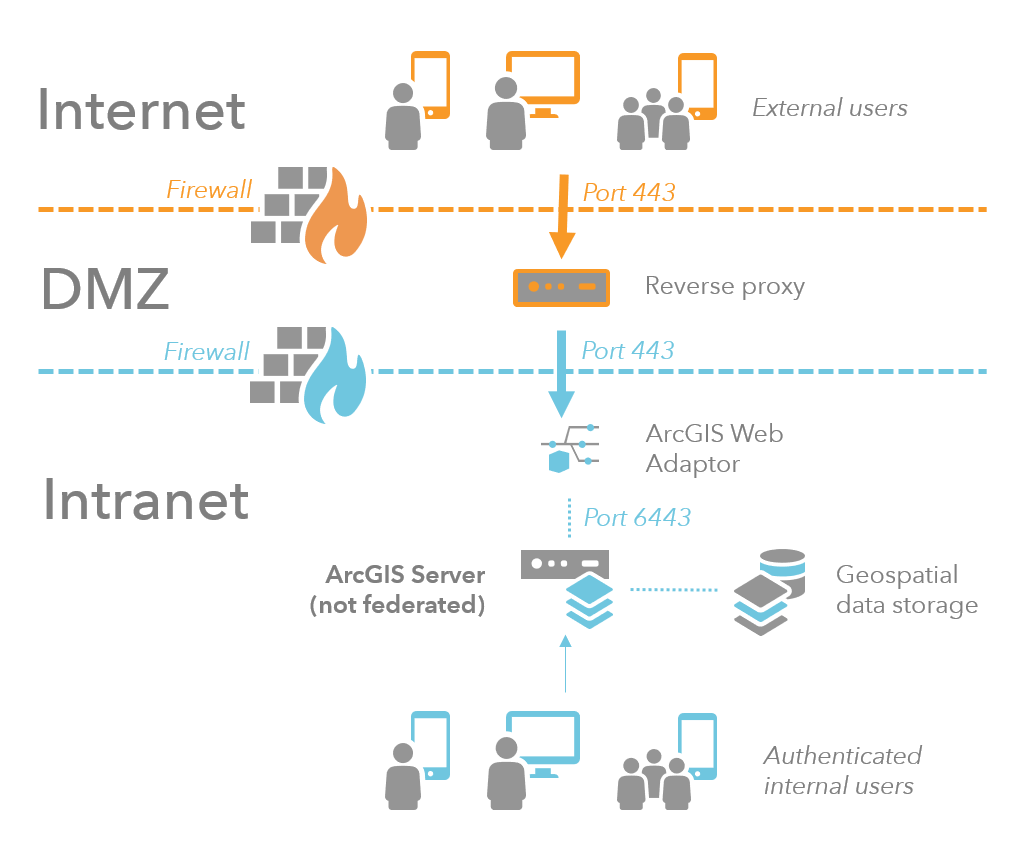
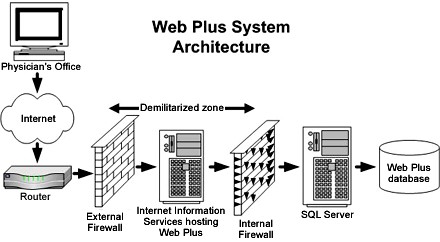
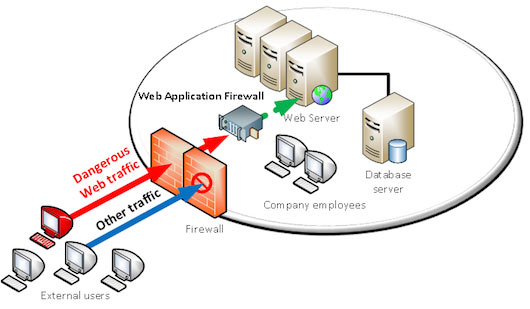
What is the best practice for placing database servers in secure network topologies - Information Security Stack Exchange
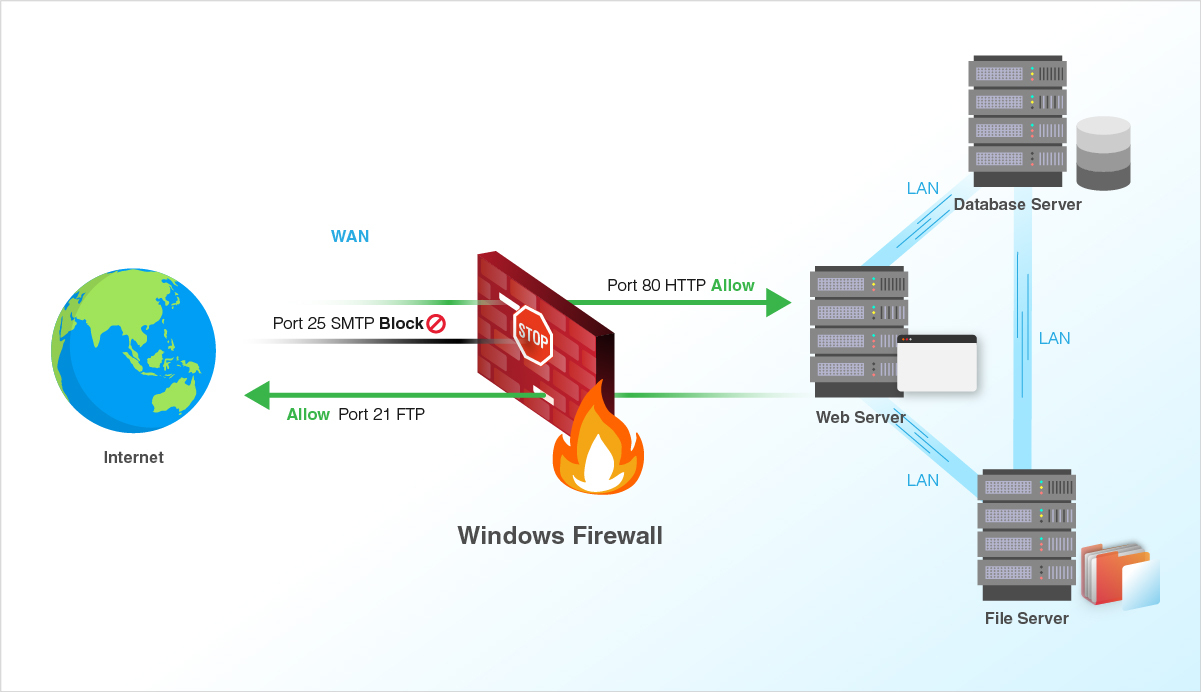
LayerStack Tutorials - LayerStack - Setting up Windows Firewall with Advanced Security on Windows Server 2019

1: Architectural diagram for the case study experiment. The attacker... | Download Scientific Diagram