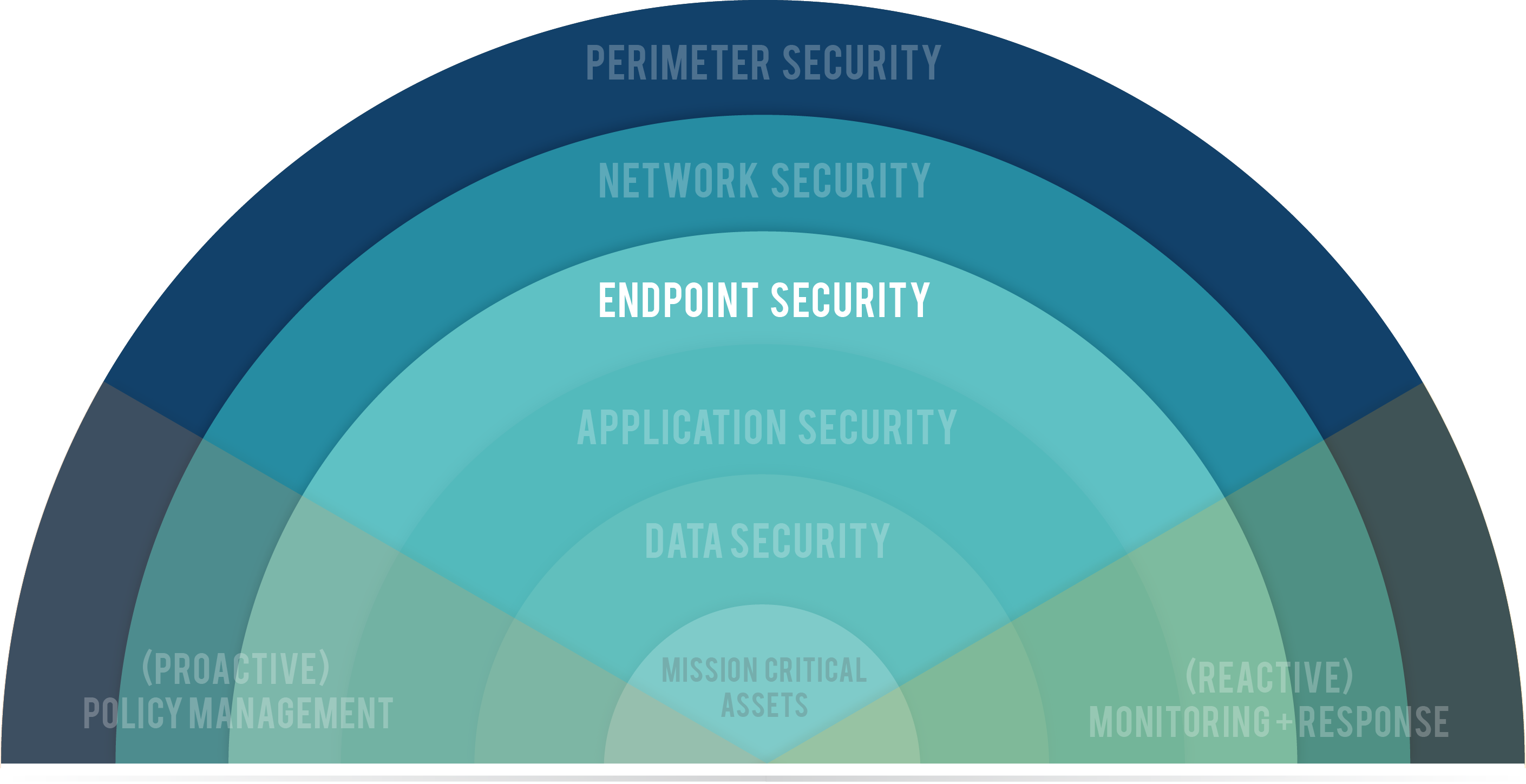
Cloud Generation Endpoint Security – Protect Your Users Everywhere and On All Devices | Symantec Blogs

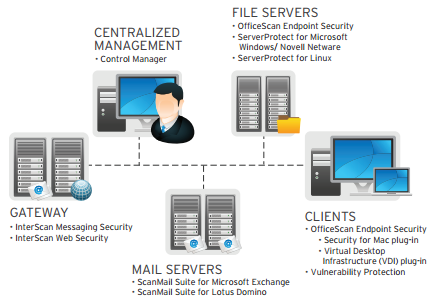
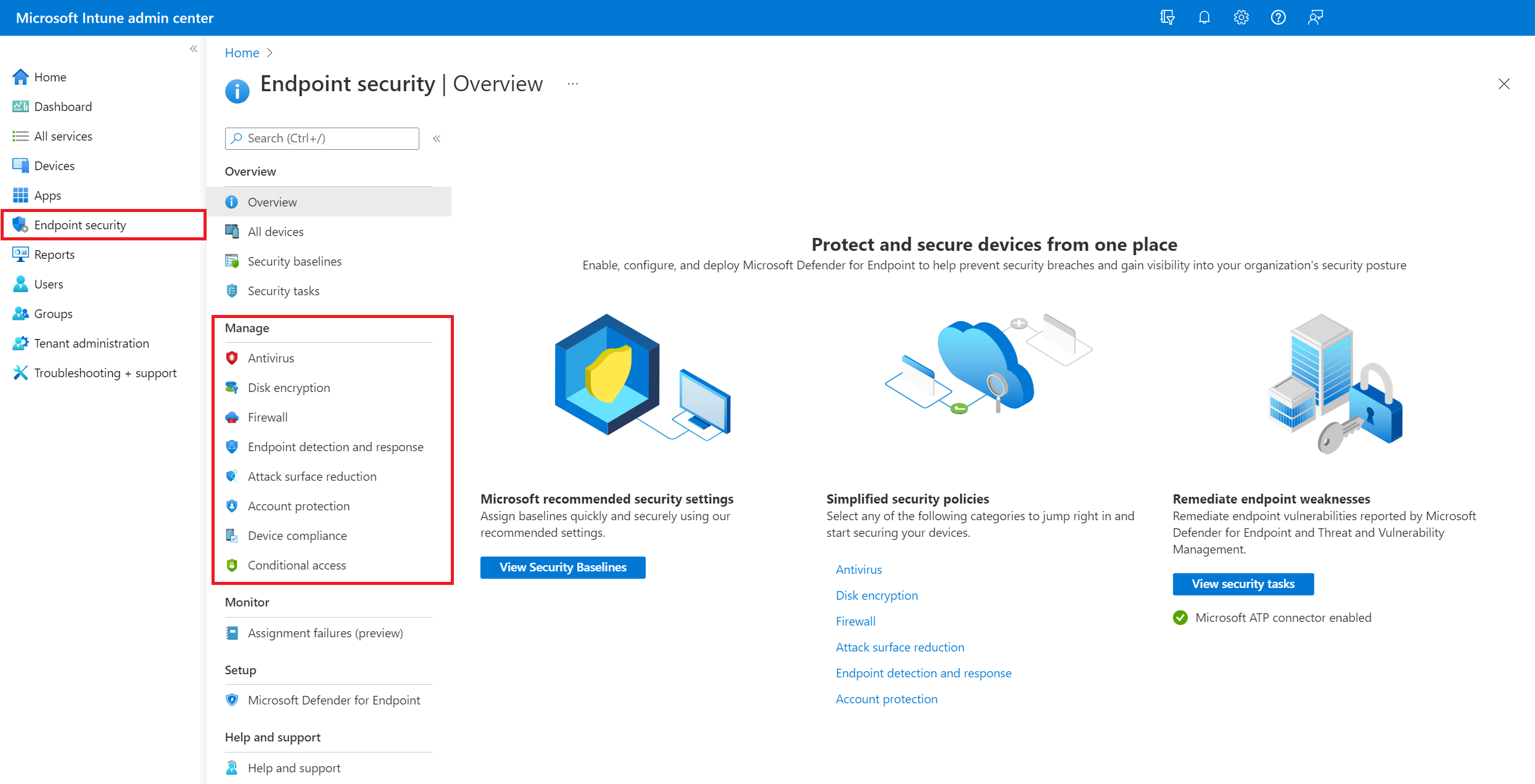
Protected endpoint applications provide common security posture for enterprise cloud ecosystems | Dave Waterson on Security

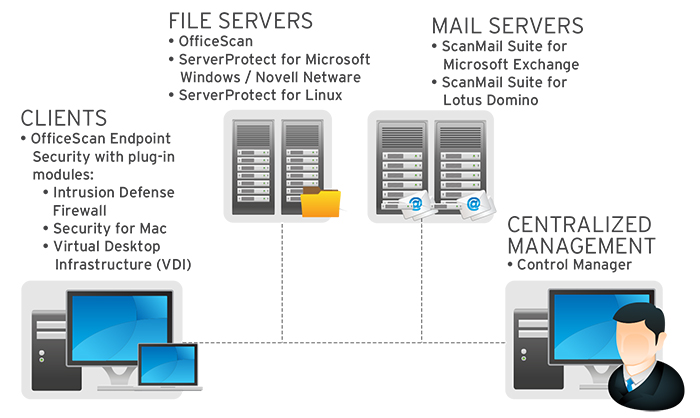
Trend Micro Enterprise Security f/Endpoints Light v10.x, GOV, RNW, 251-500u, 32m, ML Government (GOV) Renewal Multilingual
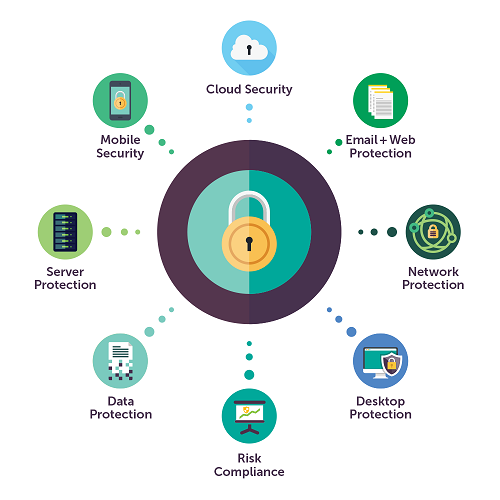
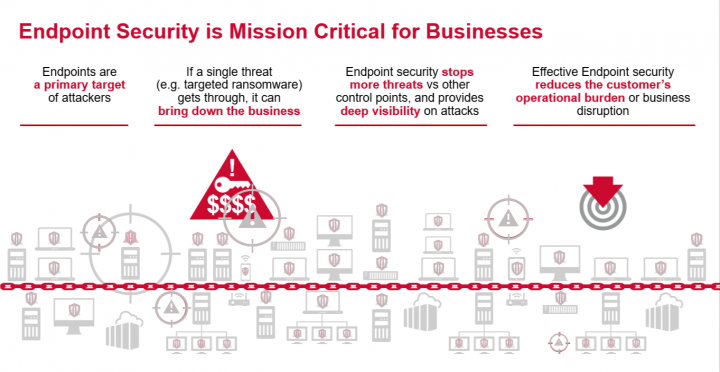
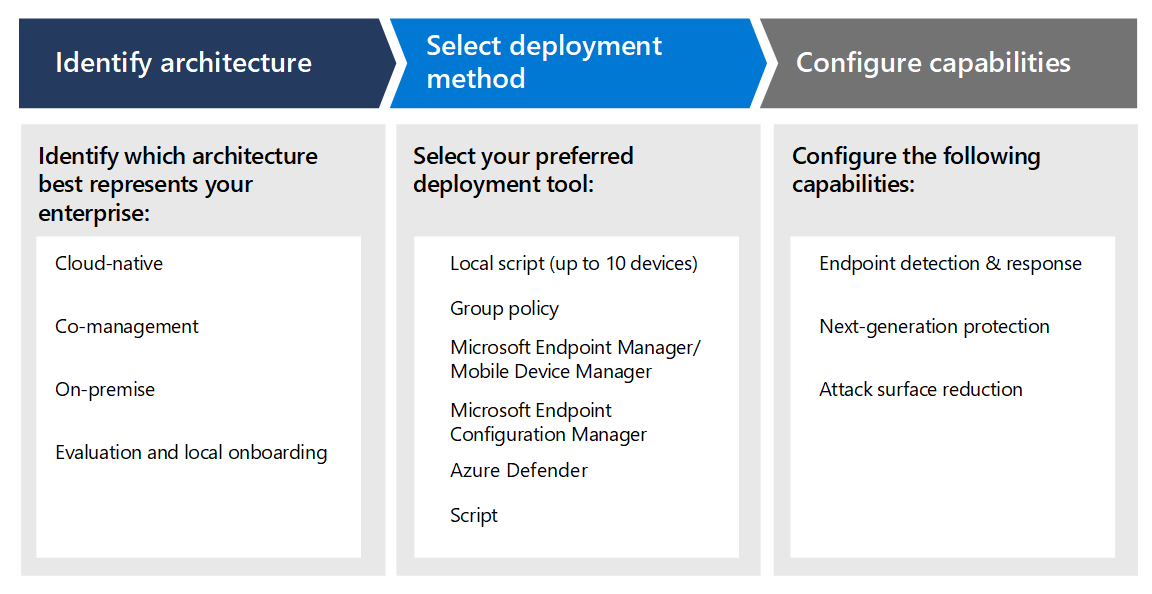
Enterprise Endpoint Security – Rules to Protect from Advanced Malware and Security Breaches – Xorlogics

CrowdStrike Falcon Continues Impressive Record with Highest AAA Rating in SE Labs Enterprise Endpoint Protection Report | crowdstrike.com






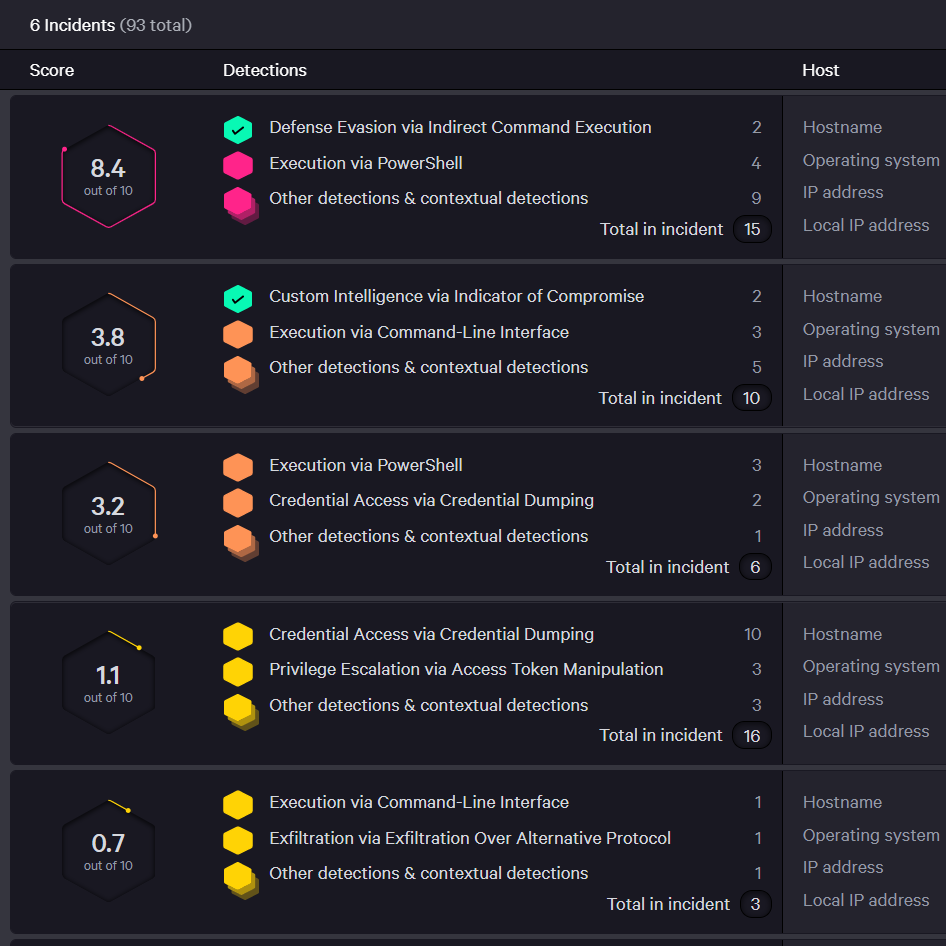

![Endpoint Detection and Response: Top 6 EDR Tools Compared [2022] Endpoint Detection and Response: Top 6 EDR Tools Compared [2022]](https://www.cynet.com/wp-content/uploads/2019/07/Endpoint-Detection-and-Response-EDR-table.png)