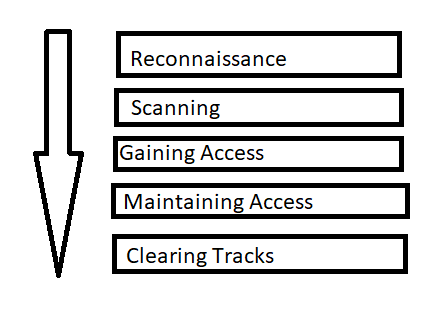
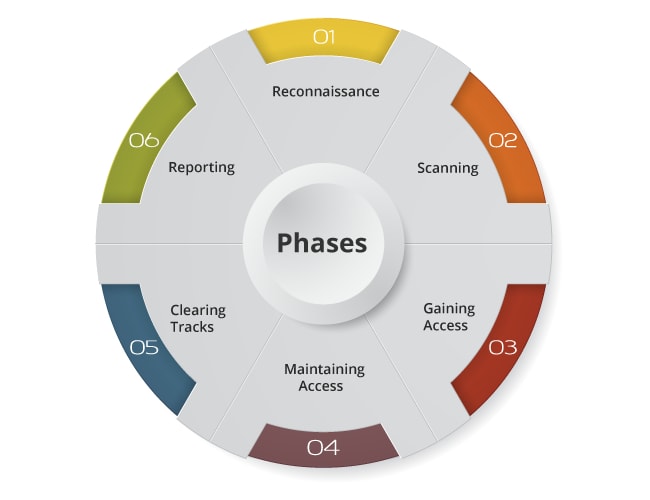
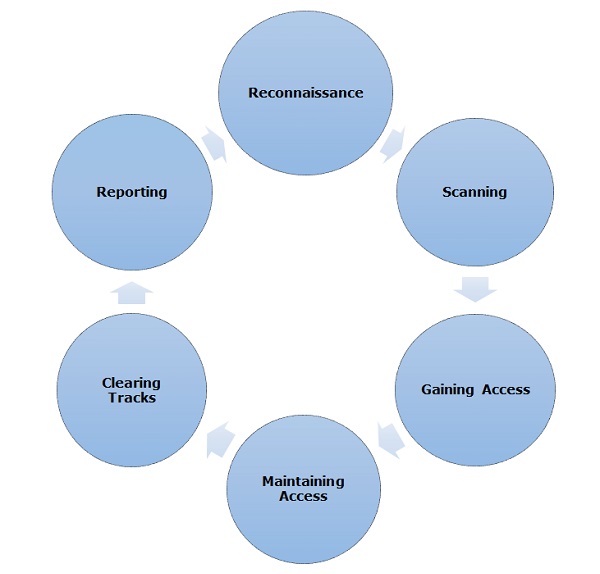
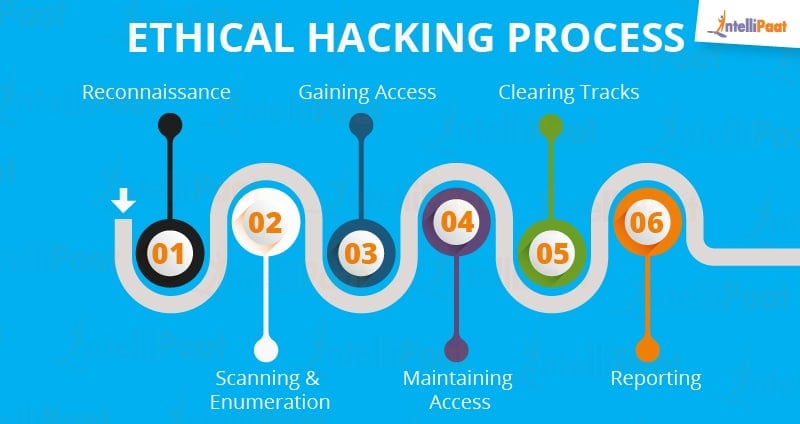
Hacker Combat™ on Twitter: "Five Phases Of Hacking #hacking #privacy #informationsecurity #cybersecurity #infosecurity #mondaythoughts #MondayVibes https://t.co/XhnP2PWprn" / Twitter
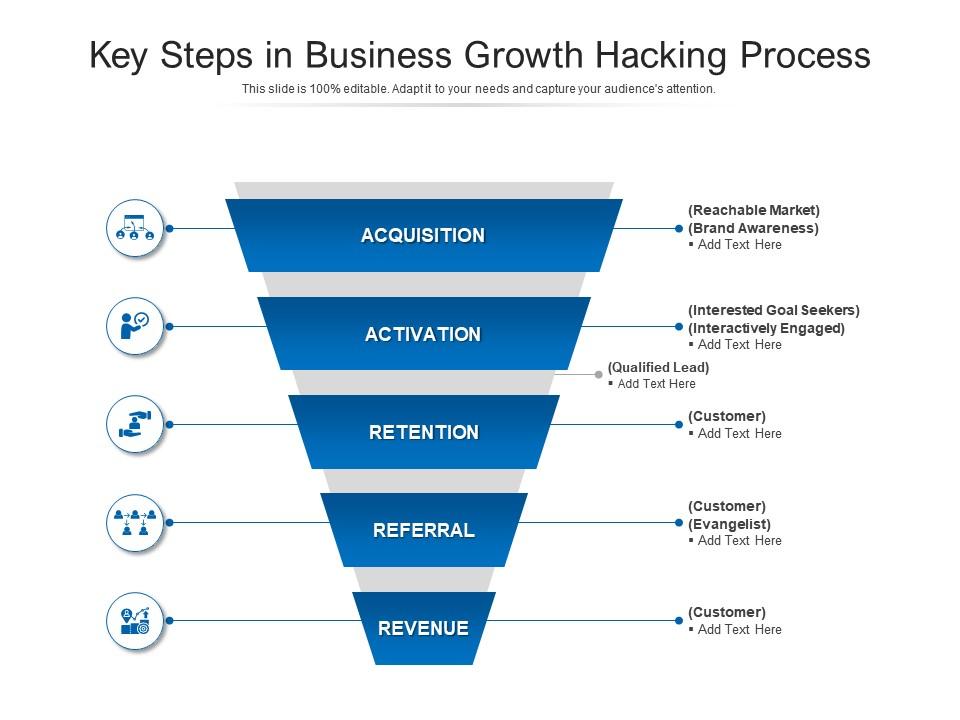
Key Steps In Business Growth Hacking Process | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

Hacking with AWS: incorporating leaky buckets into your OSINT workflow - Malwarebytes Labs | Malwarebytes Labs

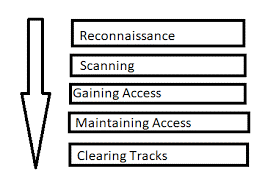
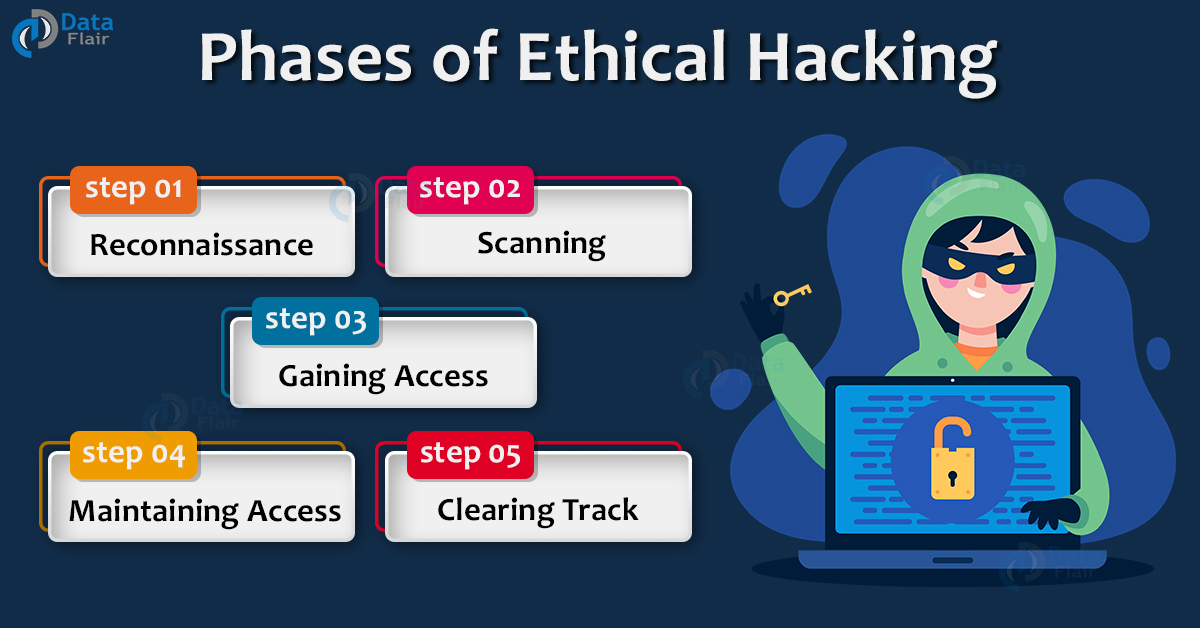
Hacking Steps Reconnaissance Scanning Covering Tracks | PowerPoint Design Template | Sample Presentation PPT | Presentation Background Images