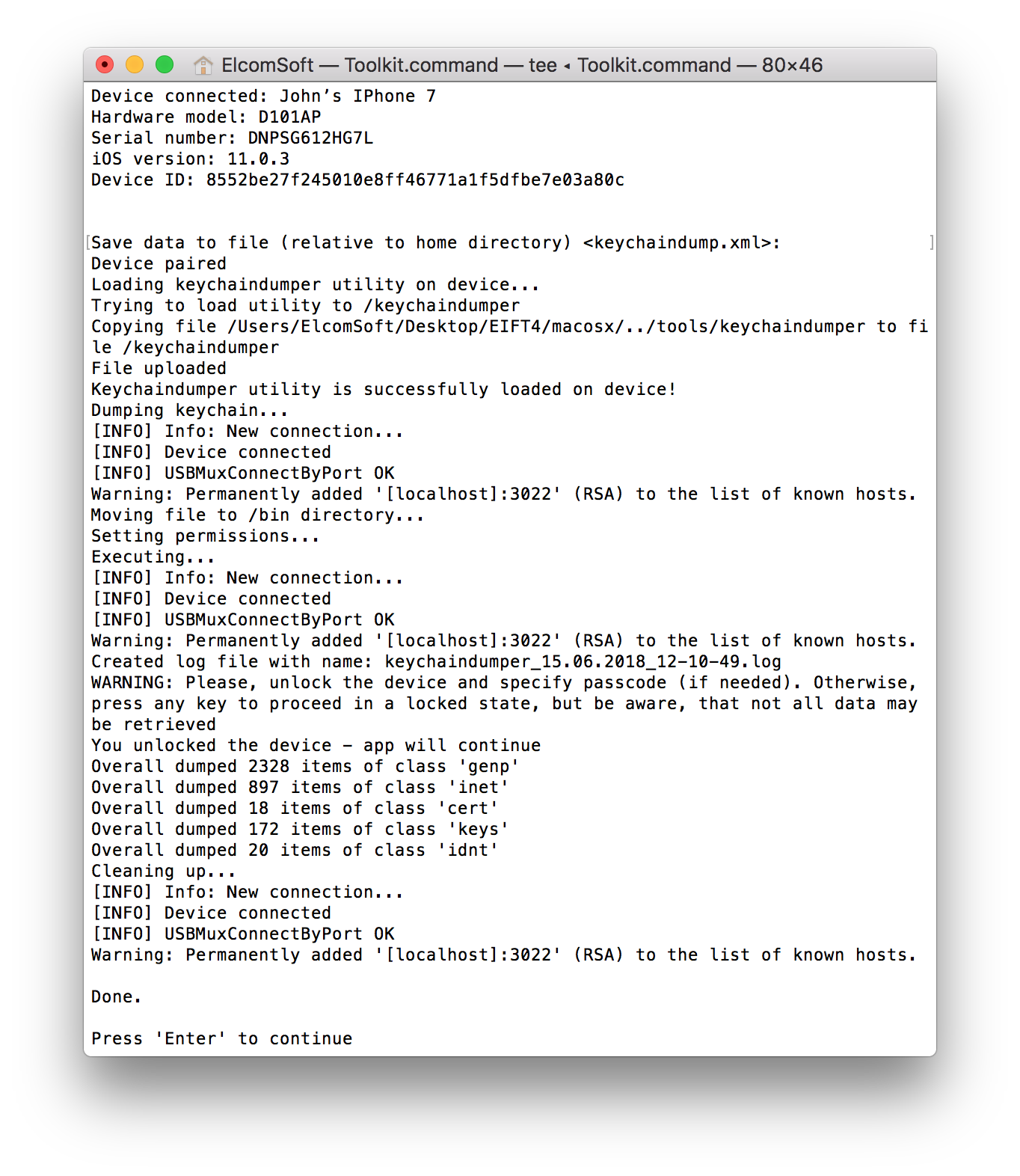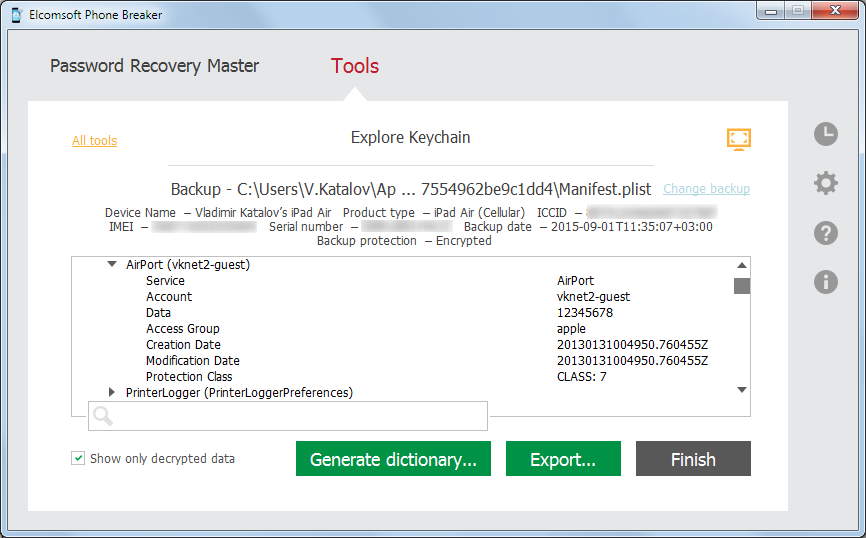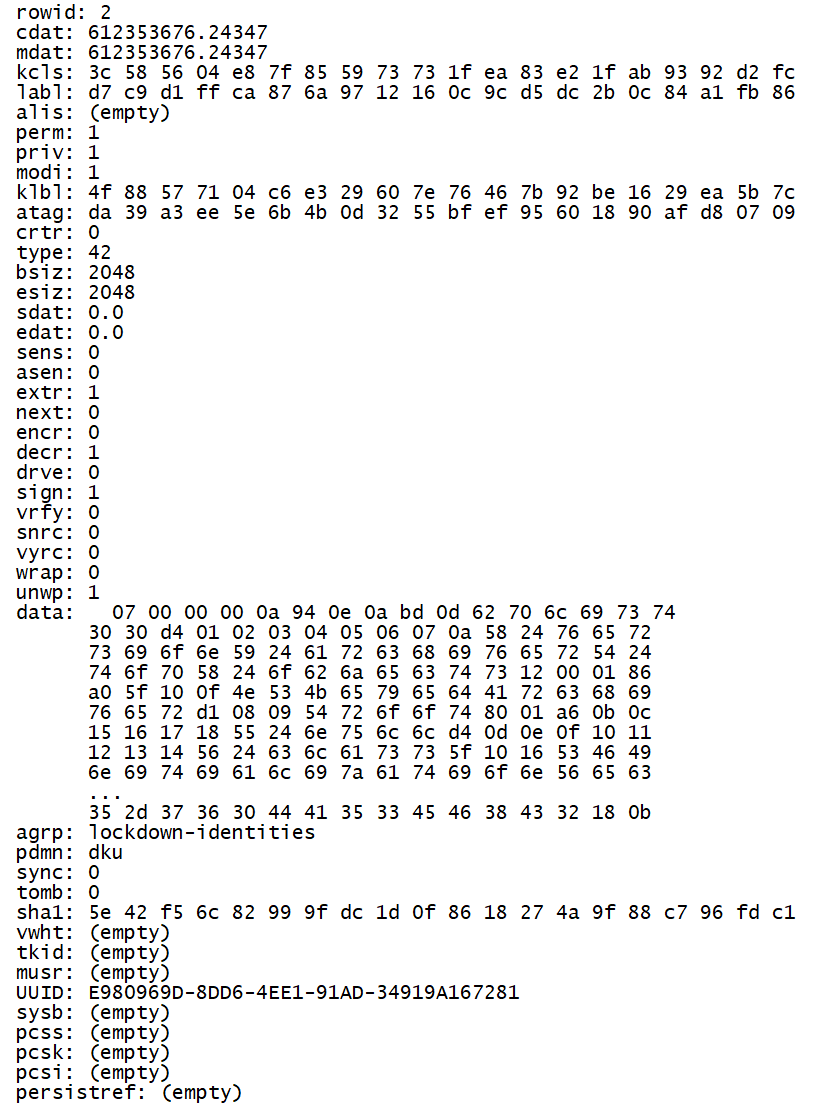
Extracting and Decrypting iOS Keychain: Physical, Logical and Cloud Options Explored | ElcomSoft blog

Extracting and Decrypting iOS Keychain: Physical, Logical and Cloud Options Explored | ElcomSoft blog

Extracting and Decrypting iOS Keychain: Physical, Logical and Cloud Options Explored | ElcomSoft blog
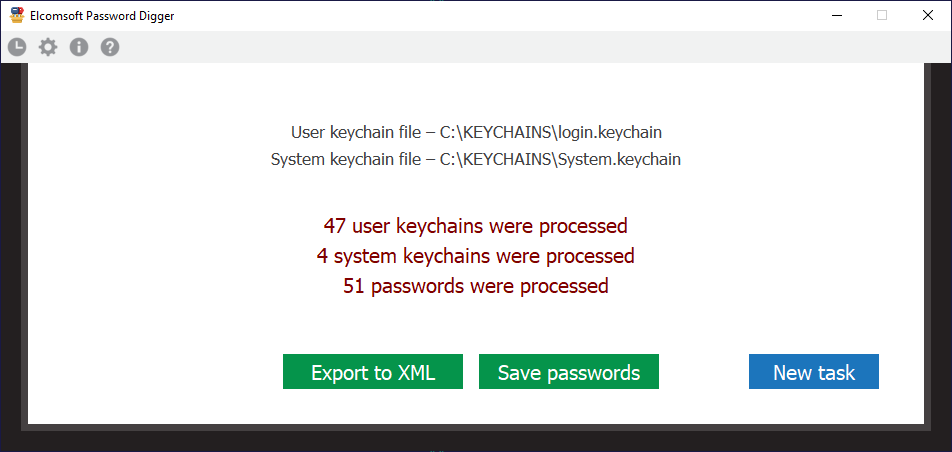
Extracting and Decrypting iOS Keychain: Physical, Logical and Cloud Options Explored | ElcomSoft blog
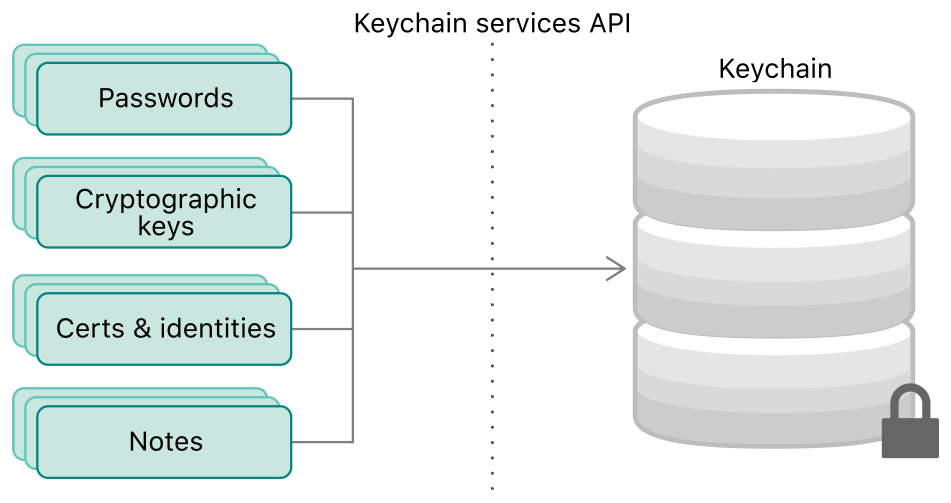
Extracting and Decrypting iOS Keychain: Physical, Logical and Cloud Options Explored | ElcomSoft blog
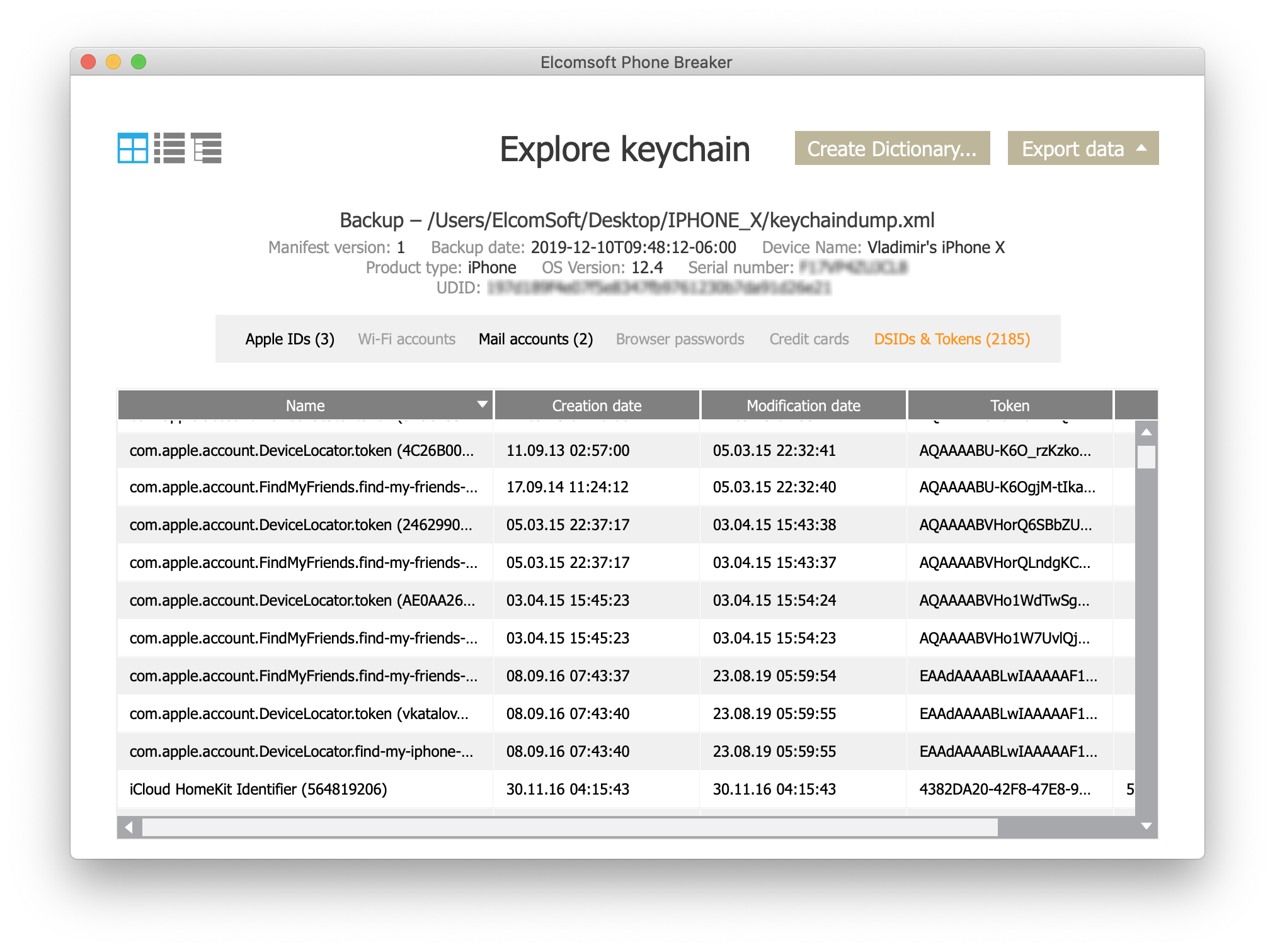
Extracting and Decrypting iOS Keychain: Physical, Logical and Cloud Options Explored | ElcomSoft blog
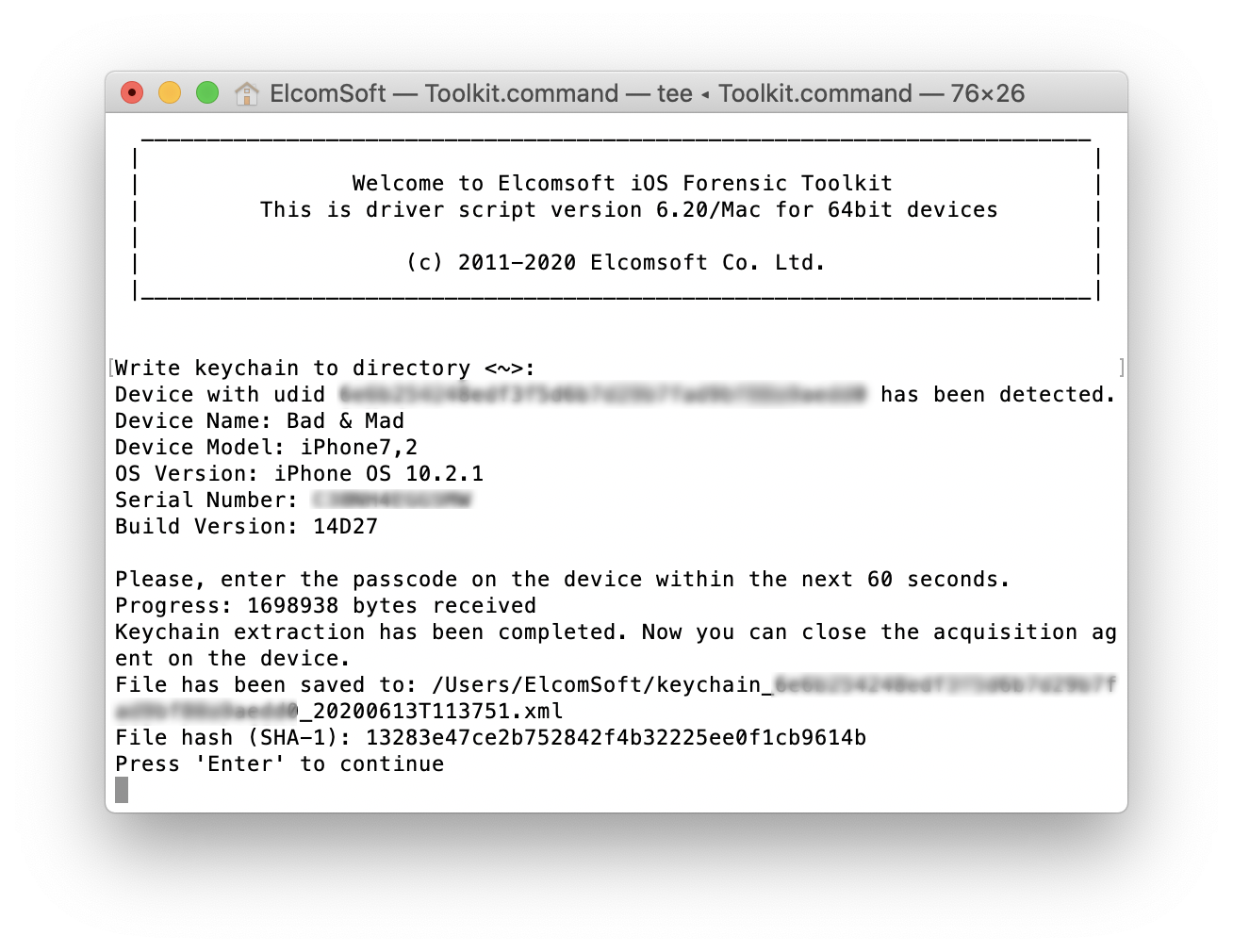
Extracting and Decrypting iOS Keychain: Physical, Logical and Cloud Options Explored | ElcomSoft blog