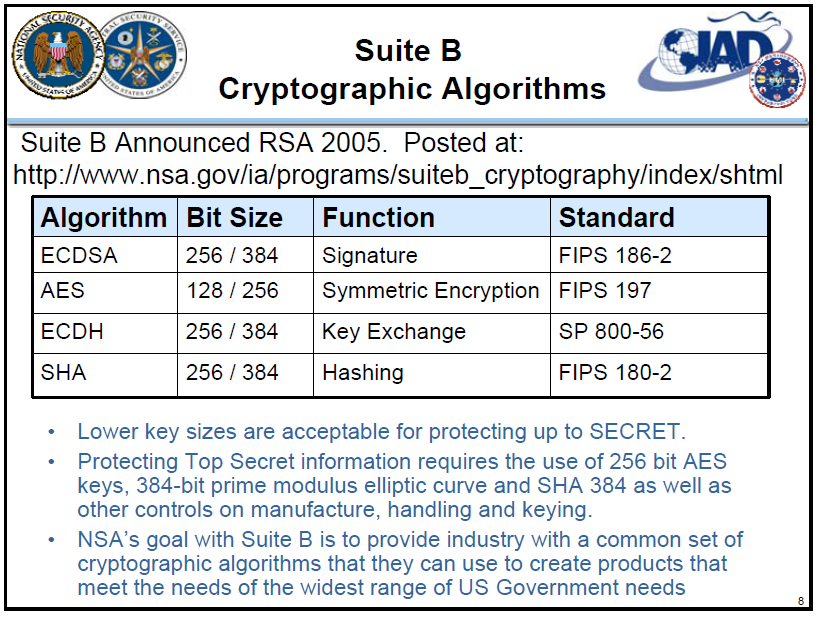
More than just cryptography: The performance advantages of Suite B compliance - Military Embedded Systems
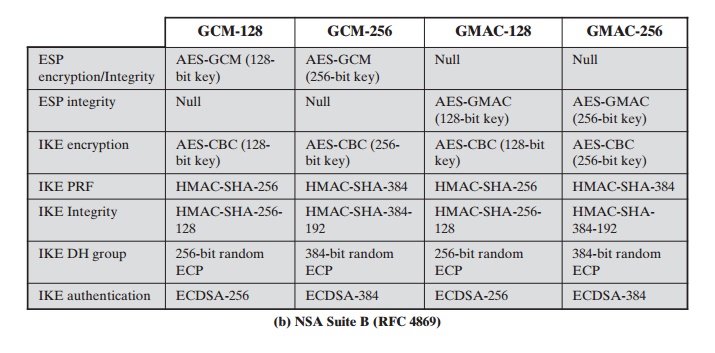
Suite-B Encryption RFC6379 - Suite-B-GCM-128 / Suite-B-GCM-256 - VPN: Site to Site and Remote Access - UTM Firewall - Sophos Community
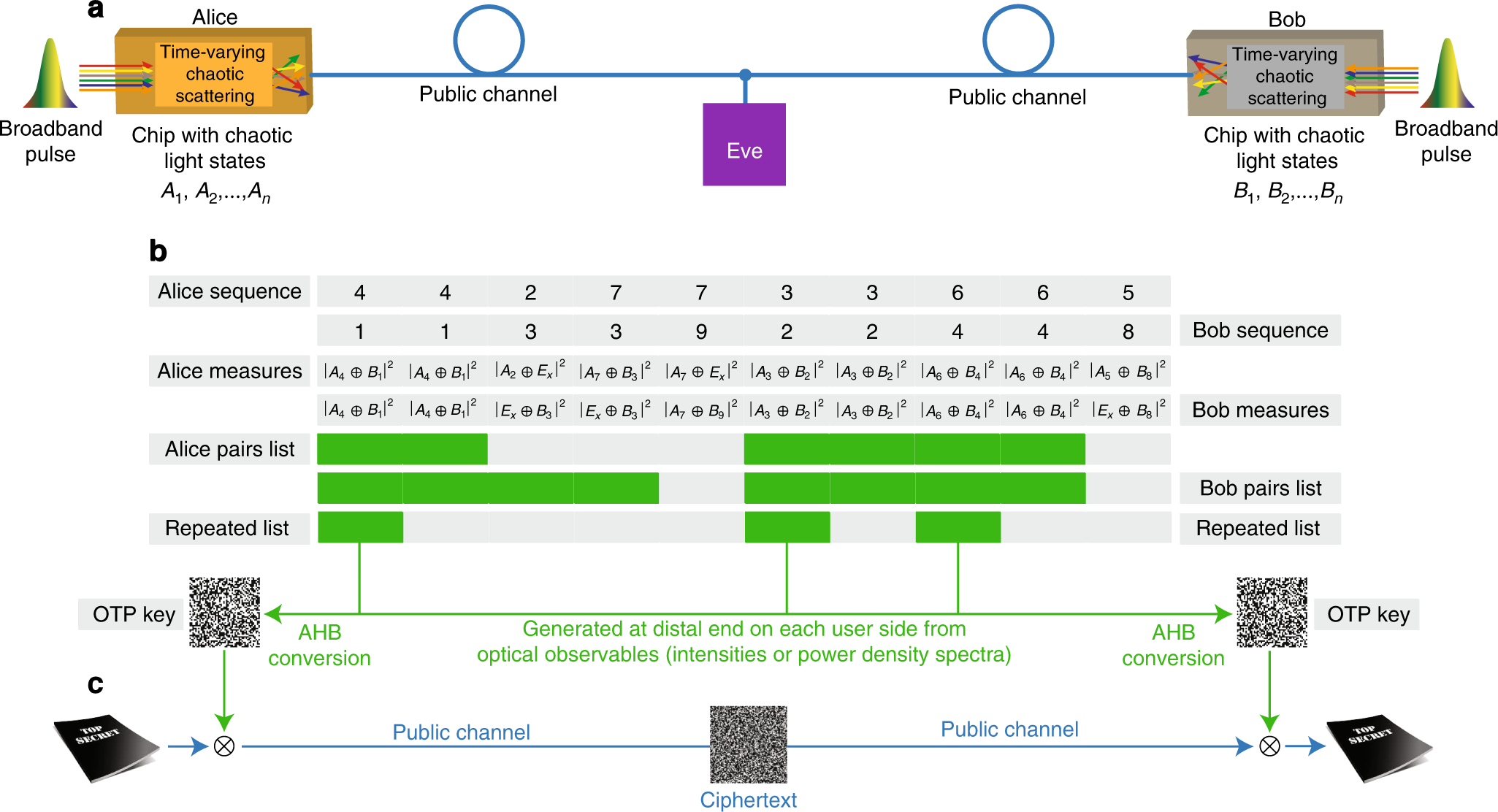
Perfect secrecy cryptography via mixing of chaotic waves in irreversible time-varying silicon chips | Nature Communications


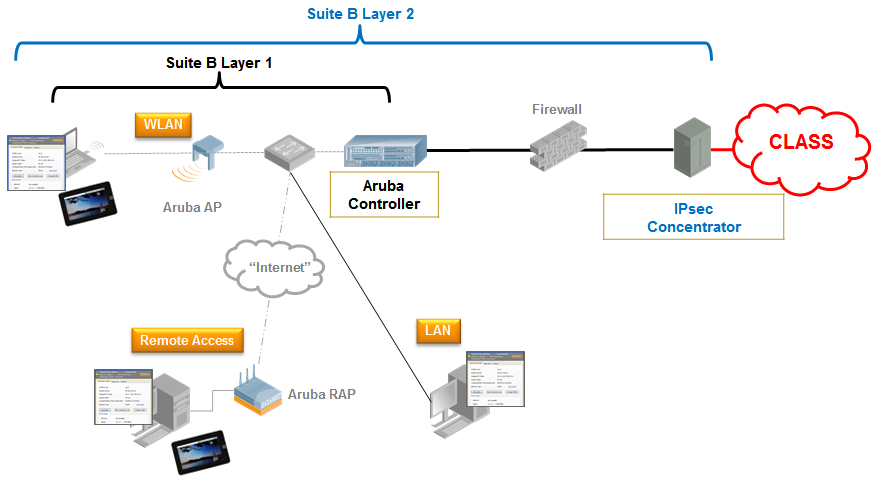


![PDF] Suite B Cryptographic Suites for Secure Shell (SSH) | Semantic Scholar PDF] Suite B Cryptographic Suites for Secure Shell (SSH) | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/d27872cc52341adf392c2295a45daf06688b5cb2/5-Table1-1.png)