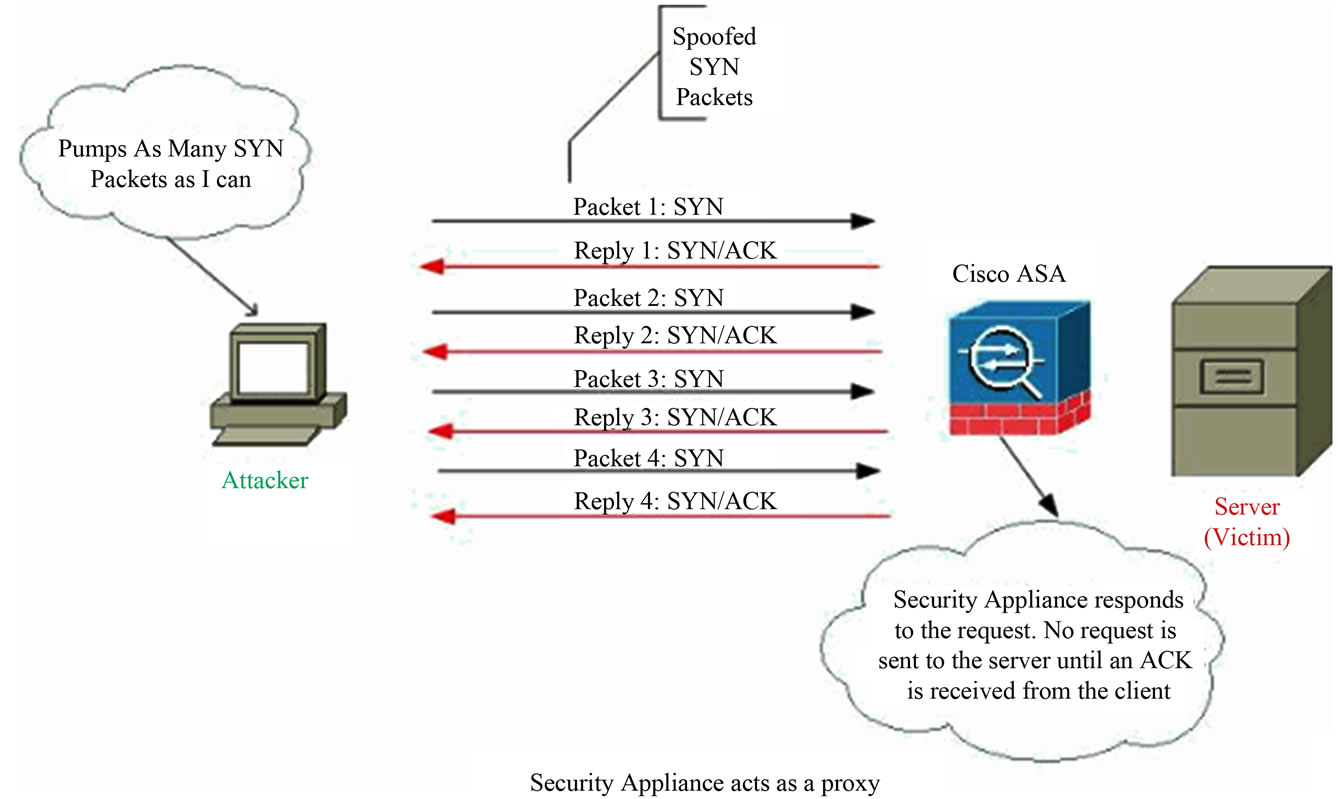
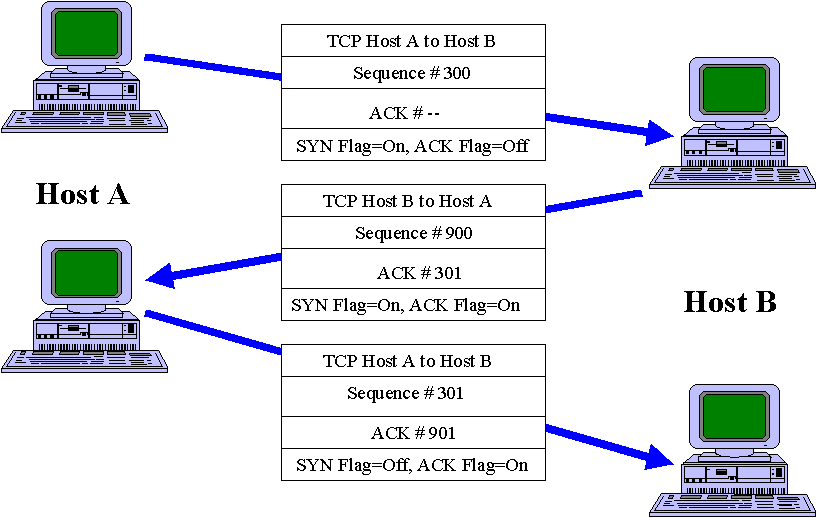
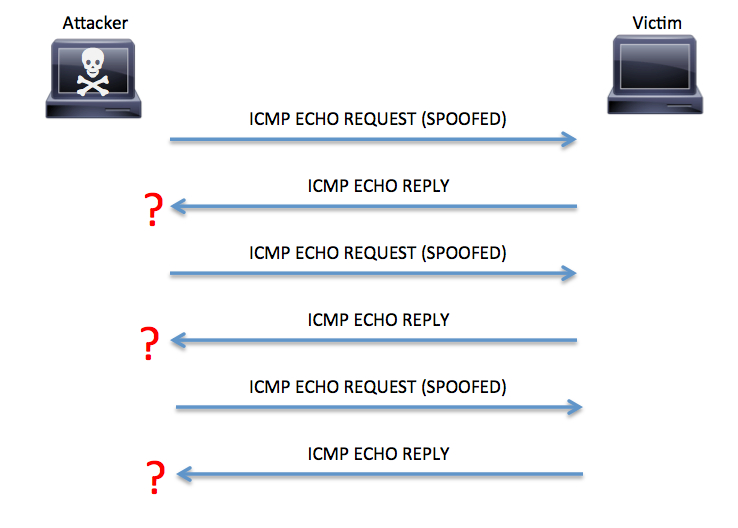
![CLI Book 2: Cisco ASA Series Firewall CLI Configuration Guide, 9.6 - Connection Settings [Cisco ASA 5500-X Series Firewalls] - Cisco CLI Book 2: Cisco ASA Series Firewall CLI Configuration Guide, 9.6 - Connection Settings [Cisco ASA 5500-X Series Firewalls] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/200001-300000/250001-260000/251001-252000/251155.jpg)
CLI Book 2: Cisco ASA Series Firewall CLI Configuration Guide, 9.6 - Connection Settings [Cisco ASA 5500-X Series Firewalls] - Cisco

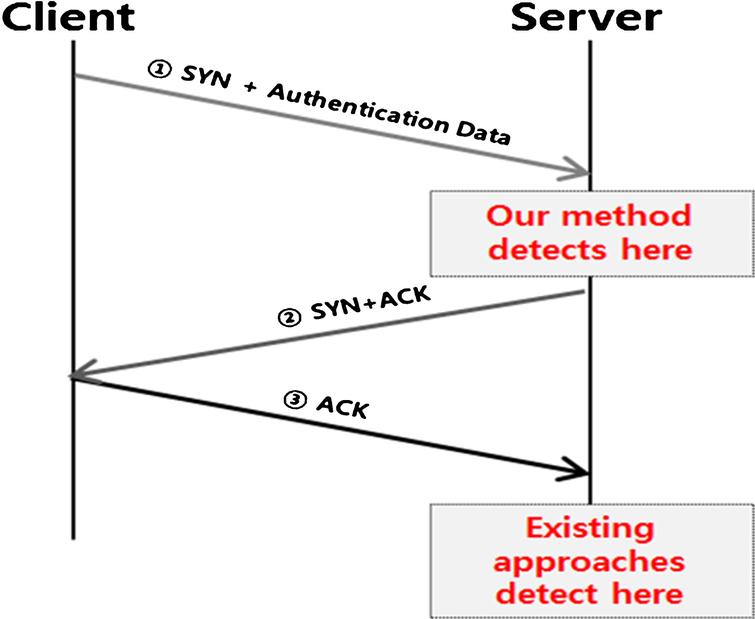
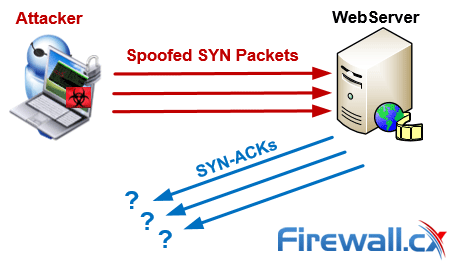
SYN flooding attack detection by TCP handshake anomalies - Bellaïche - 2012 - Security and Communication Networks - Wiley Online Library